Naval Communications in WWI
Signal Flags
Despite the recent introduction of radio communications, there was still a heavy reliance on the communications techniques used by Nelson at Trafalgar – flags.

This is Nelson’s famous signal at the battle of Trafalgar flying from HMS Victory on the bicentenary of the Battle of Trafalgar (1805).
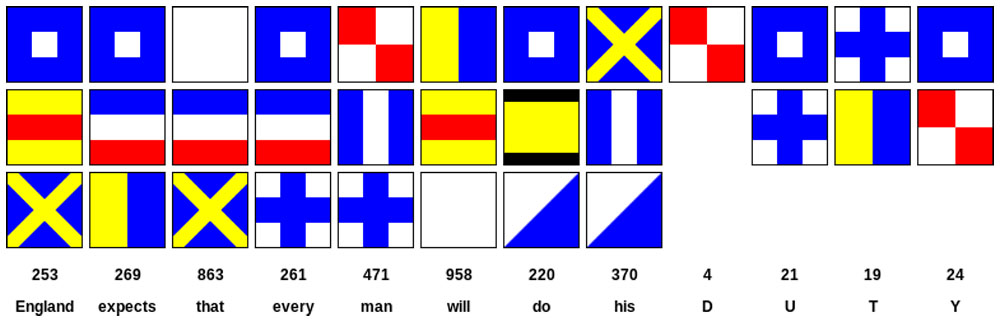
These are the groups of flags that make up the message – England expects that every man will do his duty.
Each flag represents one letter of the alphabet – see the chart below – but groups of flags are are used to represent individual words. There are 39 letters in Nelson’s message, but only 31 flags in the message. “Duty” had to be spelt out letter by letter, because there was not a code for “duty” in the signal book.
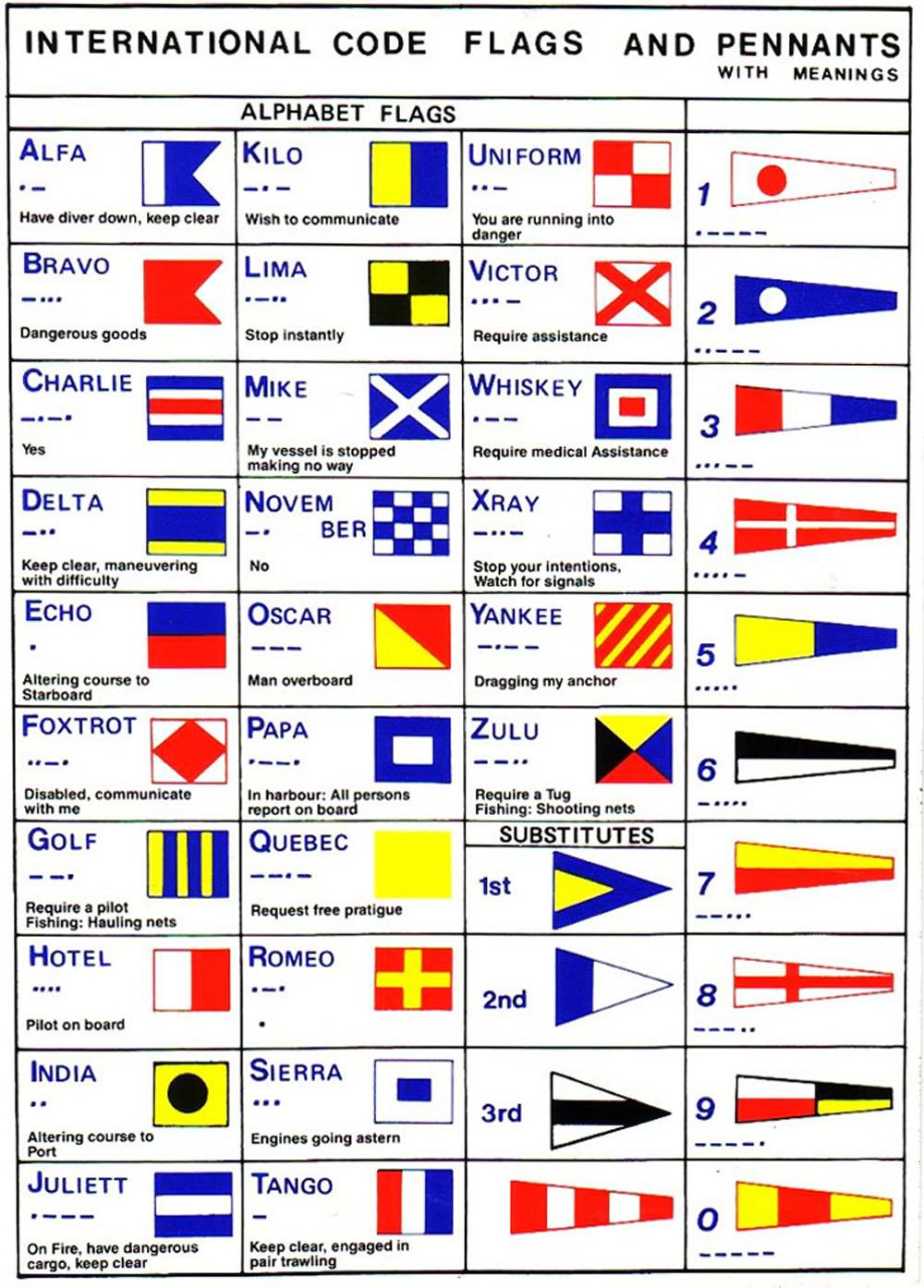
Here are the modern signal flags with their associated letters.
You can see that even sending a short message requires a lot of flags. This needs a lot of halyards – the ropes on which the flags are hoisted.
In Nelson’s time ships had lots of mast, so could carry lots of halyards.
Modern ships and those from WWI have fewer masts and fewer halyards. So long, or even short, messages have to be broken down into short blocks, and each block is sent in sequence.
There is also a navy protocol that when an order is transmitted from ship to ship – for example from the Admiral’s flagship to his accompanying fleet – the order is to be executed when the flags are hauled down.
There were many cases of confusion in battles caused by signalling errors. The Admiral would issue an order to be transmitted. For example “head north east at full speed and engage the enemy destroyers.” The signaller would then have to make this message as short as possible, and using as many standard signals from the signal book as possible to speed communications, so it might become “course NE full speed attack destroyers.” Then the message would be turned into blocks of flags, hoisted up in turn, and then the last block would be hauled down when the Admiral wanted the fleet to change course.
This all gave room for confusion. First of all, the flags can be difficult to see if the ships are any distance apart. Then there is room for misinterpretation. Does “attack destroyers” mean that the destroyers are to attack or are enemy destroyers to be attacked?
Finally, not all commanders used the same signalling protocols. Jellicoe ran things by the book, while Beatty had a more relaxed approach. This caused problems in the Battle of Jutland, when Beatty’s cruisers were augmented by a squadron of battleships that had previously only worked with Jellicoe. At one point in the battle Beatty signalled a change of course to his fleet. The signal was hoisted, and stayed hoisted. The cruisers were used to reading signals then watching for the flag ship to turn, and then following the lead, without waiting for the flags to be hauled down. The commander of the battle ship squadron kept his ships sailing on the wrong course for ten minutes, waiting for the signal flags to be pulled down. By the time he did change direction he was out of touch with the cruisers.
You can try your hand at sending signals by flag at the Fisherman’s Hut next to the Light Tower. Or you can go to South Queensferry and try reading these flag signals from the Museum..
Morse Code
Morse Code was invented in the 1840s as a way to send Telegraph messages over an electric cable strung from one location to another. When the telegram sender closed a switch, an electric current flowed along the electric cable, and at the far this was used to create a mark on a paper tape. The longer the sender’s switch was closed, the longer the mark on the paper at the receiver. Each letter of the alphabet was represented or coded, by a sequence of short and long pulses of current. A short pulse of current, made by closing the sender’s switch for a short time, produced a short mark on the paper – a “dot.” A longer pulse of current, made by closing the sender’s switch for a longer time, produced a long mark on the paper – a “dash.”

The early operators of this system soon discovered that they could hear the sound created by the receiving device as it made dots and dashes on the paper, and could tell dots from dashes. They did not need the marked paper, they could “decode” each letter by sound as it was received, and write down the received message in plain language.
Morse code can be transmitted in a number of ways. As well as the original method of sending electrical pulses along a telegraph wire, it can also be send as a radio signal with short and long tones, or as a flashing light with short and long flashes, or even in mine rescue work as short and long pulls on a rope.
Aldis Lamp
The Navy used a device called an Aldis lamp, to send Morse Code message between ships. The Aldis lamp is a mini search-light which shines a tight beam of light from one ship to another. It has a set of shutters, much like a Venetian blind, that are operated by a lever on the side of the lamp. Opening the shutters for a short time sends a “dot”, opening them for a longer time sends a “dash”

Aldis lamps are still used today. They are a fairly secure means of communication, because the narrow beam of light can only be seen from the direction in which it is pointed.
Radio Communication
During the 1860s, the Scottish physicist, James Clerk Maxwell predicted the existence of radio waves, and in 1886, German physicist, Heinrich Rudholph Hertz demonstrated the transmission and reception of a radio signal in his laboratory.
Work continued to turn this phenomenon into a technology. It was Guglielmo Marconi, an Italian inventor, who proved the feasibility of radio communication.
He sent and received his first radio signal in Italy in 1895. By 1899 he flashed the first wireless signal across the English Channel and in 1902 received the letter “S”, telegraphed from England to Newfoundland.
Marconi was already sending Morse Code by radio.
Clearly this technology was useful to Armies and Navies. Radio signals could be transmitted a long way, from one ship to another and from ship to shore. Morse code transmitters and receivers are fairly simple devices, it would be many decades before voice transmission by radio was practicable.
But the very advantage of radio, being able to receive a radio signal over a great distance, is also a disadvantage, because anyone can tune in and receive the transmission.
Secret Codes
The solution was to use codes and ciphers. Morse code is one example, where letters and numbers are represented by sequences of dots and dashes, the Flag signals discussed above are another. But these are international codes, so anyone can read the signal and decode the message.
To transmit a message securely, i.e. without a third party being able to decode the message, even if they have received if, a secret code is required.
There are two kinds of secret code pre-arranged messages and encryption.
Pre-arranged messages
Admiral von Reuter used two pre-arranged messages to order the sinking of his ships in Scapa Flow.
These were “Paragraph 11, acknowledge” which meant send men to man the sea valves and then he sent “Condition Z” which meant open the sea-valves and scuttle the ships.
Pre-arranged messages are useful for specific situations, but they lack flexibility, von Reuter had no means of sending “scuttle only the destroyers.”
Encryption
That problem is solved with encryption. Any message can be encrypted, by applying a code to each individual letter in the message. The message can only be decrypted if the recipient knows how it was encrypted, i.e. they know the key to the encryption process.
One simple encryption or coding technique is letter substitution, where one letter is swapped for another, and the simplest for of this is known as Caesar’s code or Caesar shift. To encode a message, you swap each letter in the original “plaintext” for another letter which is a fixed shift along the alphabet.
A shift-4 code would send ABC as EFG – each letter is shifted four letters along the alphabet
Here is a shift-23 code, and a message in “plaintext” i.e. the original message and “ciphertext” the encrypted message.
Plain: ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher: XYZABCDEFGHIJKLMNOPQRSTUVW
Plaintext: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG
Ciphertext: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD
The terms code, cipher and encryption all have subtly different meanings for experts, but are often used interchangeably.
Code-breaking
Codes, in a various forms and disguises, have been used by people and governments for centuries and still very much in use today to maintain secrecy.
Code breaking is an art as well as a science that should suit those who enjoy solving crossword or Sudoku puzzles. Sharp minds are required for challenges that sometimes have to be faced especially if, breaking a particular code, the fate of a nation depends.
The German electronic cipher machine called Enigma, was first patented by the inventor Arthur Scherbius in 1918, that could theoretically produce 159 million million million combination of letters. This machine was widely used by the German military in WW2 but the code deciphering and decryption activity was centred on the top-secret location at Bletchley Park. It is estimated that the work of the code breakers of Bletchley Park with the help from Polish mathematicians, who were the first to determine how the Enigma machine worked, shortened WW2 by at least a year.
The fore-runner of Bletchley Park in WWI was Room 40.
Room 40
Before 1914, international communication was conducted via undersea cables, most under British control, laid along shipping lanes. Hours after the British ultimatum to Germany in August 1914, the British cut German cables and messages could only be passed by wireless, using ciphers to disguise their content.
The Signalbuch der Kaiserlichen Marine (SKM) was captured from the German light cruiser SMS Magdeburg, after it ran aground in the Baltic on 26 August 1914.
The German-Australian steamer Hobart was seized near Melbourne, Australia on 11 August and the ship’s Handelsverkehrsbuch (HVB) codebook, used by the German navy to communicate with merchant ships and within the High Seas Fleet, was captured; a copy of the book was sent to England by the fastest steamer, arriving at the end of October.
During the Action off Texel 17 October 1914, the commander of the German destroyer SMS S119 threw overboard all secret papers in a lead lined chest as the ship was sinking. On 30 November, a British trawler dragged up the chest, which was passed on to Room 40, a copy of the Verkehrsbuch (VB) codebook, normally used by Flag officers of the Kaiserliche Marine being found inside.
The Director of the Intelligence Division of the Admiralty, Rear-Admiral Henry Oliver established a code breaking organisation to decipher German signals, using cryptographers from academic backgrounds, making use of the windfalls taken from the German ships. At first, the inexperience of the cryptanalysts in naval matters led to errors in the understanding of the material and this lack of naval experience caused Oliver to make personal decisions about the information to be passed to other departments, many of which, particularly the Operations Department, had reservations about the value of Room 40.
The transfer of an experienced naval officer, Commander W. W. Hope, remedied most of the deficiencies of the civilians’ understanding but on 14 October, Oliver became Chief of the Naval War Staff and continued to treat Room 40 more as a fiefdom and a source for the informal group of officers around the First Lord of the Admiralty, Winston Churchill, which received decoded messages but had insufficient authority to use them to best advantage.
German ships had to report their position every night by wireless and listening posts built along the British east coast took cross-bearings to find the positions of the ships when they transmitted.
The signals intelligence meant that the British did not need wasteful defensive standing patrols and sweeps of the North Sea. The British could economise on fuel and use the time for training and maintenance.
The Admiralty also uncovered the German order of battle and tracked the deployment of ships, which gave them an offensive advantage.
The lack of a proper war staff at the Admiralty and poor liaison between Room 40, Oliver and the operations staff, meant that the advantage was poorly exploited in 1915. (It was not until 1917 that this was remedied.)
When German ships sailed, information from Room 40 needed to be passed on quickly but Oliver found it hard to delegate and would not routinely supply all decrypts. Oliver’s reticence meant that the Admiralty supplied commanders at sea only what the Admiralty thought they needed, risking information reaching the Grand Fleet late, being incomplete or mistakenly interpreted. When Jellicoe asked for a decryption section to take to sea, it was refused on security grounds.
Need to know
This “need to know” problem persists today. In both WWI and WWII, the Germans were convinced that their codes could not be broken and sent all sorts of “interesting” messages by radio. In WWII, the decrypted messages from Bletchley Park were known as “Ultra” and the information was used very sparingly, so that the Germans would not realize that their codes had been broken. If every time they sent an order to their Army and Navy and the men or ships were immediately ambushed, they would rapidly become suspicious, and then might change the codes making decoding very difficult or impossible.
Only a select few commanders were made aware of the full significance of Ultra.
A famous WWI case of code-breaking concerned the Zimmermann Telegram. This encrypted telegram from Berlin to the German Ambassador in Mexico was intercepted and decrypted by British Intelligence, and the plaintext was passed to the US Government. But how could the British explain how they obtained the intelligence without revealing that they could intercept and decode supposedly secure encrypted telegrams? The answer was to create a cover story.
The British claimed that they had stolen a copy of the plain-text message after it had been decrypted in the German Embassy in Mexico.
This caused the Embassy staff to launch a witch-hunt to find the traitor in their embassy.
Communications Exhibition at the Fisherman’s Hut
As part of our exhibition and events the code section will be based at the ‘Fisherman’s Hut’ located next to the light tower on the North Queensferry Town Pier.
The ‘Hut’ is the base for our amateur radio station operating under the call sign GB1FB broadcasting on the 40 and 20 metre amateur bands in both speech and Morse Code which a visitor will be able to see and hear in action and possibly participate in the operation.
Around the ‘hut’ area there will be signal flags on display with a message which will require decoding. For those visitors to the exhibition in the Queensferry Museum, with whom we are co-operating, and may not be able to travel to North Queensferry then subject to weather the flags may be visible with the aid of a telescope or binoculars.
Messages written in code on paper for deciphering with a WW1 theme will also be available at all venues taking part on both sides of the river.
Codes for Code breaking will be available later this year at a time to be announced on our website and other social media.
Format will be: to use Morse Code, Signal Flags and other code styles, in an encrypted form, all for you to solve and hand in your answers to either the venue staff or via email direct to us at our dedicated address.
To help prepare to decipher some of the puzzles you will need to know the basic Morse Code and Signal Flag symbols plus the summarised history of the Aldis Lamp.
Prizes and certificates of competence will be awarded in 2019 to those who can meet the challenge of code breaking.
top of page
